HUB Security SPAC Presentation Deck
What is Confidential Computing?
9
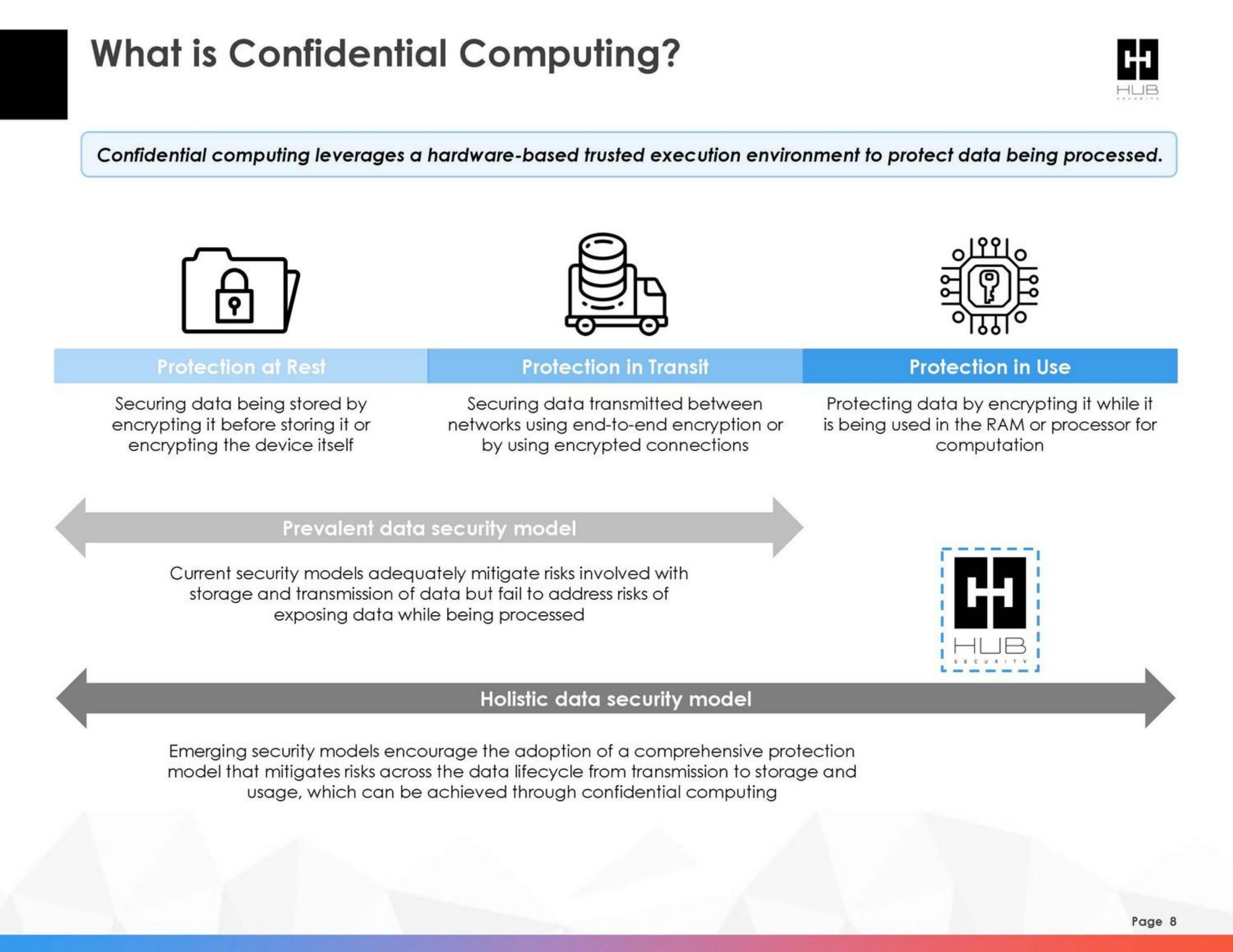
Confidential computing leverages a hardware-based trusted execution environment to protect data being processed.
Protection at Rest
Securing data being stored by
encrypting it before storing it or
encrypting the device itself
Protection in Transit
Securing data transmitted between
networks using end-to-end encryption or
by using encrypted connections
Prevalent data security model
Current security models adequately mitigate risks involved with
storage and transmission of data but fail to address risks of
exposing data while being processed
19⁹10
Holistic data security model
Emerging security models encourage the adoption of a comprehensive protection
model that mitigates risks across the data lifecycle from transmission to storage and
usage, which can be achieved through confidential computing
I
HUB
Protection in Use
Protecting data by encrypting it while it
is being used in the RAM or processor for
computation
H
HUB
SECURI
Page 8View entire presentation